
Recently, WikiLeaks has leaked the CIA’s entire bunch of hacking tools. Guess what the most interesting thing about these tools that are actually leaked by the WikiLeaks is, these tools are actually used by the CIA to spy on smartphones, computers and even televisions which are now available for download.
WikiLeaks Publishes CIA’s Entire Collection Of Hacking Tools
The revelations that Edward Snowden made, and which exposed the NSA’s ways of acting and tools, showed the world that government agencies are not always what they are.
After this case became known and the world was shaken, a new one emerged, brought by WikiLeaks and revealing the tools the CIA uses to spy on smartphones, computers and even televisions.
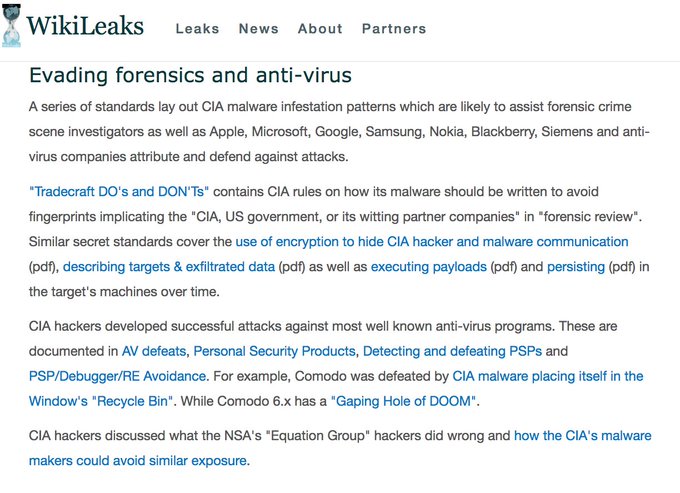
WikiLeaks unveiled Vault 7, a file set consisting of a total of 8,761 documents from the CIA, the United States Intelligence Agency. These documents contain lines of code that allow those who own them to have the CIA’s ability to hack into an iOS system, Android, and many others. WikiLeaks considers these documents a kind of hacking arsenal, with viruses, trojans, and malware that can attack mobile devices overnight.
WikiLeaks' #Vault7 reveals gaping holes in all popular operating systems + anti-viruses programs wikileaks.org/ciav7p1/
This release is the first of a series on the CIA that WikiLeaks intends to launch to showcase the capabilities and means of the Agency. Using these techniques revealed, the CIA can transform equipment from Google, Apple, Microsoft, and Samsung, whether it be a telephone or a TV, into a microphone in disguise!
CIA negligence sees it losing control of all cyber weapons arsenal sparking serious proliferation concerns #Vault7wikileaks.org/ciav7p1/#PRESS
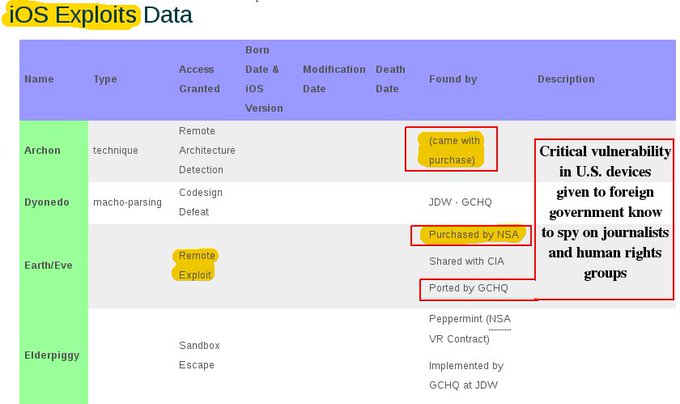
In an analysis of the documents, WikiLeaks noted that both iPhones and iPads have been targeted by the CIA and will certainly continue to be. While Android devices are a dominant force, WikiLeaks argues that the CIA’s focus on iOS is due to the popularity of the brand.
The agency has a specialized unit to create and run malware so they can extract information from Apple products. It is believed that to obtain this information extraction, there are pieces of code, unknown to the creators of the software, which contains vulnerabilities that can be exploited by hackers.
What makes this look real?
Program & office names, such as the JQJ (IOC) crypt series, are real. Only a cleared insider could know them.
If you're writing about the CIA/@Wikileaks story, here's the big deal: first public evidence USG secretly paying to keep US software unsafe. pic.twitter.com/kYi0NC2mOp
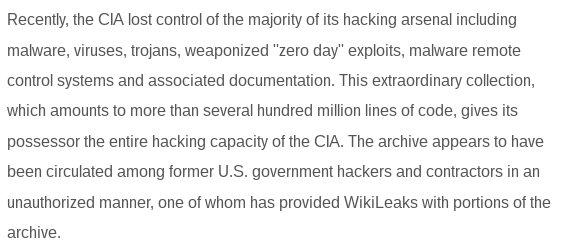
In addition to malware for affected systems, Wikileaks claims the CIA has lost control over most of its hacking material. These documents state that it is possible, through malware, to attack both an Android phone and one with Apple software. Targets go further and reach Twitter accounts.
The full list of documents can be found here, and briefly, a thorough review of the documents by security experts will let you know the impact of this information leak.





![Temple Run OZ Unlimited Coins+Gems [FULL] Free Download For Android](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhS_8lrnad05Upf0Xi0HDiT1t3JXRJYXthHdyr_ZniJzBfo4o0YV4c8R2e9qLM-8u3FydRjwh3JSTkxcfJXPbBquDjFzU8p6pj2rduOfvTZWDPosMr-ZMoVbn0NHyefI10ntTyEFSnsQtc/w100/Temple+Run+Oz+apk.jpg)


0 Comments